Please classify the following security defenses into the correct classification.

Data monitoring can be divided into two types: active analysis and passive acquisition.
The network environment is becoming more and more complex, and network security incidents occur frequently. While accelerating the construction of informatization, enterprises must not only resist external attacks, but also prevent internal management personnel from being involved in data leakage and operation and maintenance accidents due to operational errors and other issues. Which of the following options might reduce operational risk?
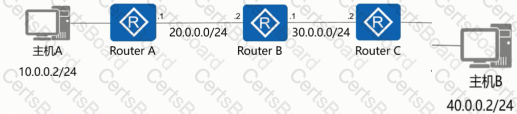
As shown in the figure, the administrator needs to test the network quality of the 20.0.0/24 CIDR block to the 40.0.0/24 CIDR block on Device B, and the device needs to send large packets for a long time to test the network connectivity and stability.
Drag the phases of the cybersecurity emergency response on the left into the box on the right, and arrange them from top to bottom in the order of execution.[fill in the blank]*

IKE SA is a one-way logical connection, and only one IKE SA needs to be established between two peers.
_____ Authentication is to configure user information (including local user's user name, password and various attributes) on the network access server. The advantage is that it is fast.[fill in the blank]*
In the TCP/P protocol core, which of the following protocols works at the application layer? ( )[Multiple choice]*