Which FortiSASE feature ensures least-privileged user access to all applications?
Which secure internet access (SIA) use case minimizes individual workstation or device setup, because you do not need to install FortiClient on endpoints or configure explicit web proxy settings on web browser-based end points?
When viewing the daily summary report generated by FortiSASE, the administrator notices that the report contains very little data.
What is a possible explanation for this almost empty report?
Refer to the exhibit.
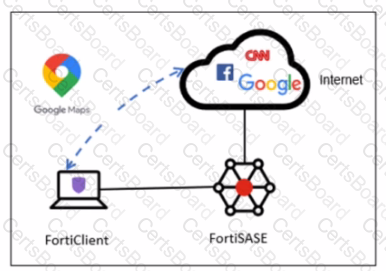
A company has a requirement to inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical Interface.
Which configuration must you apply to achieve this requirement?
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
Refer to the exhibit.
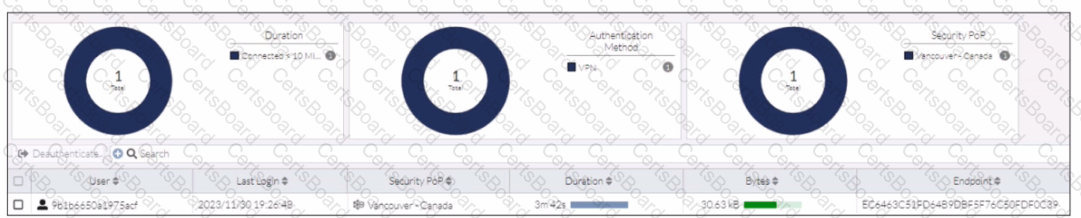
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
An organization must block user attempts to log in to non-company resources while using Microsoft Office 365 to prevent users from accessing unapproved cloud resources.
Which FortiSASE feature can you implement to achieve this requirement?
Which two statements describe a zero trust network access (ZTNA) private access use case? (Choose two.)


