Refer to the exhibit.
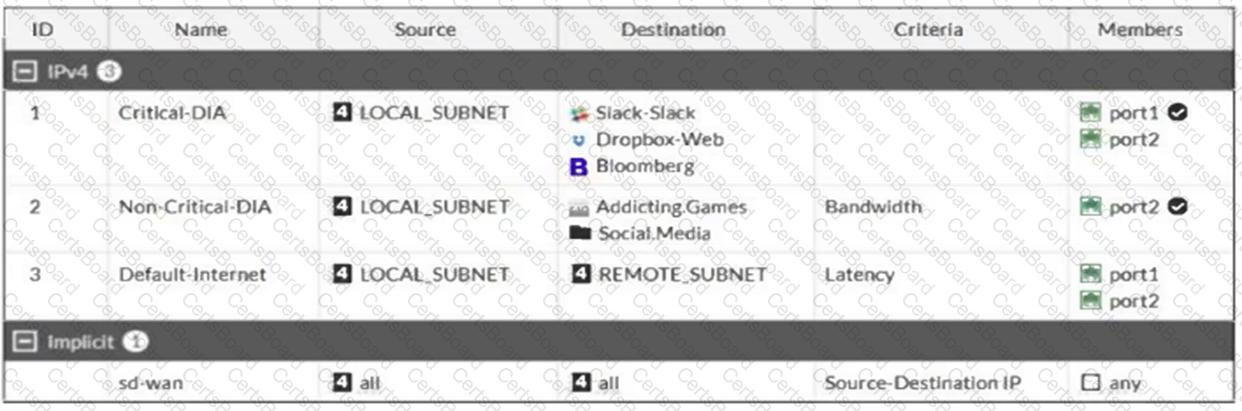
Which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules?
Refer to the exhibit.
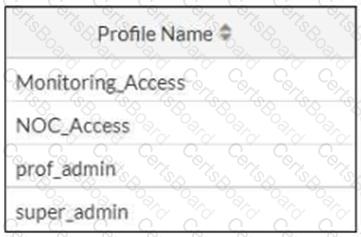
The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity.
What must the administrator configure to answer this specific request from the NOC team?
Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three.)
Refer to the exhibits, which show the system performance output and the default configuration of high memory usage thresholds in a FortiGate.
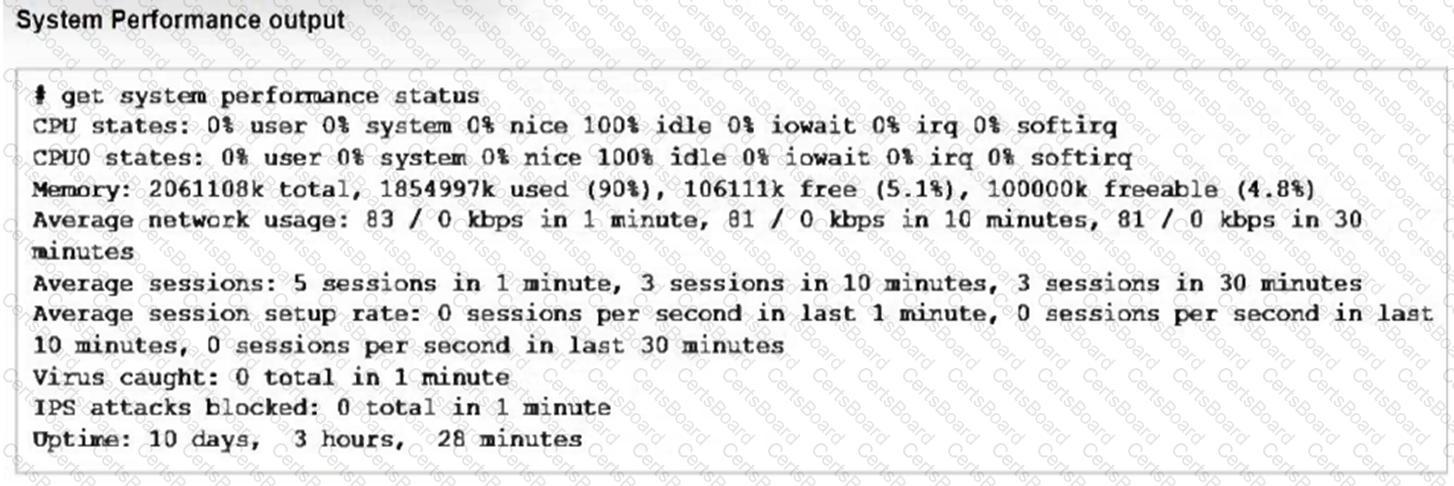
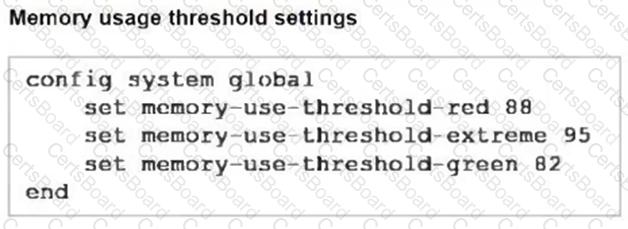
Based on the system performance output, what can be the two possible outcomes? (Choose two.)
An administrator has configured the following settings:
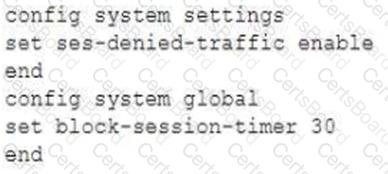
What are the two results of this configuration? (Choose two.)
Refer to the exhibits.
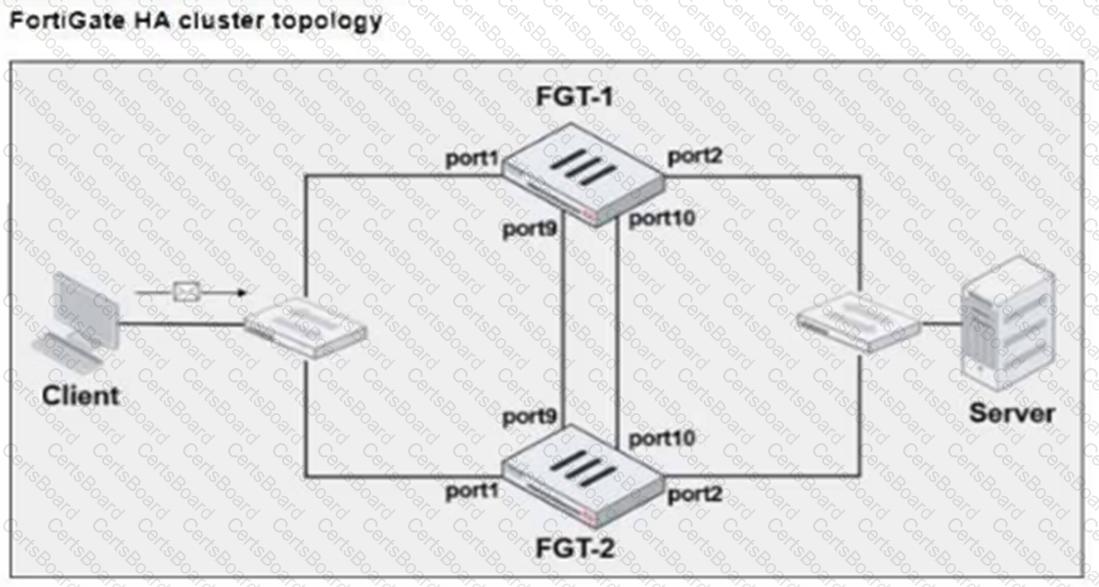
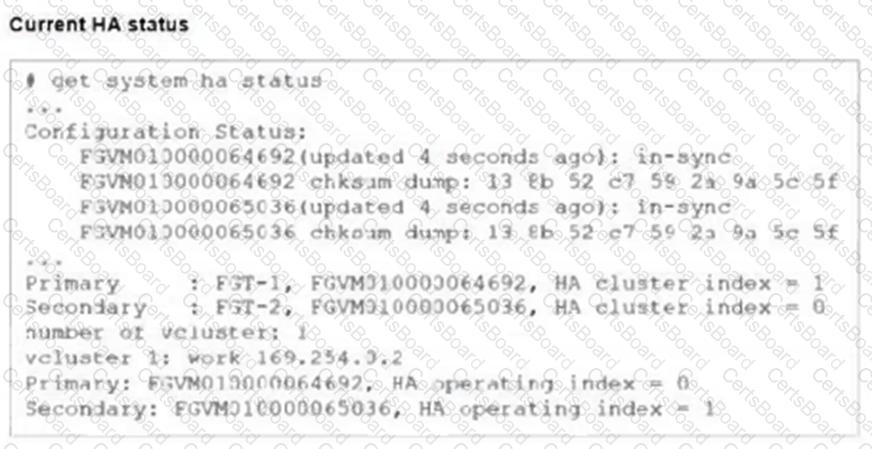
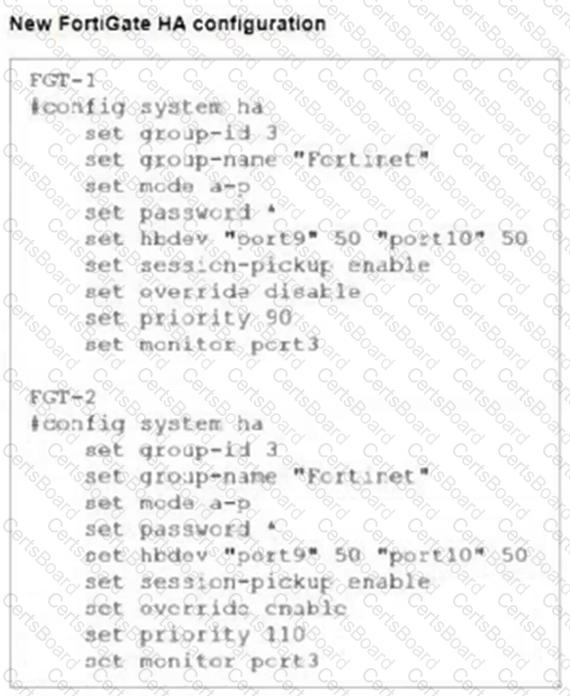
FGT-1 and FGT-2 are updated with HA configuration commands shown in the exhibit.
What would be the expected outcome in the HA cluster?
Refer to the exhibits.
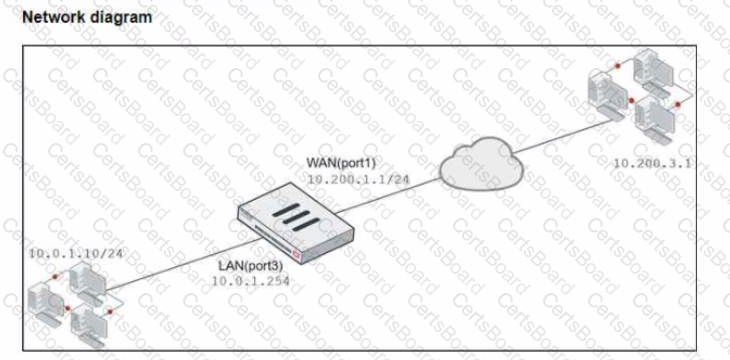
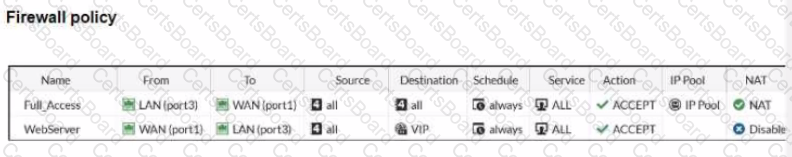
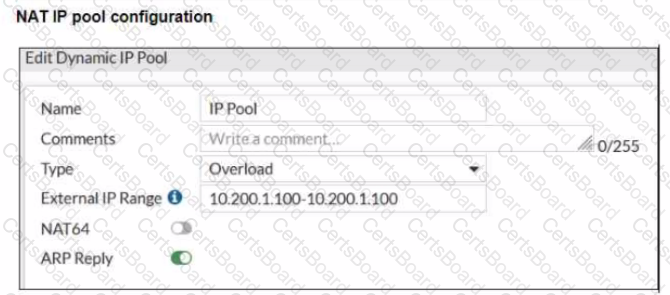
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall policies configuration VIP configuration and IP pool configuration on the FortiGate device
The WAN (port1) interface has the IP address 10.200. l. 1/24 The LAN (port3) interface has the IP address 10.0.1.254/24
The first firewall policy has NAT enabled using the IP pool The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT (SNAT) the internet traffic coming from a workstation with the IP address 10.0.1.10?
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
Refer to the exhibits.
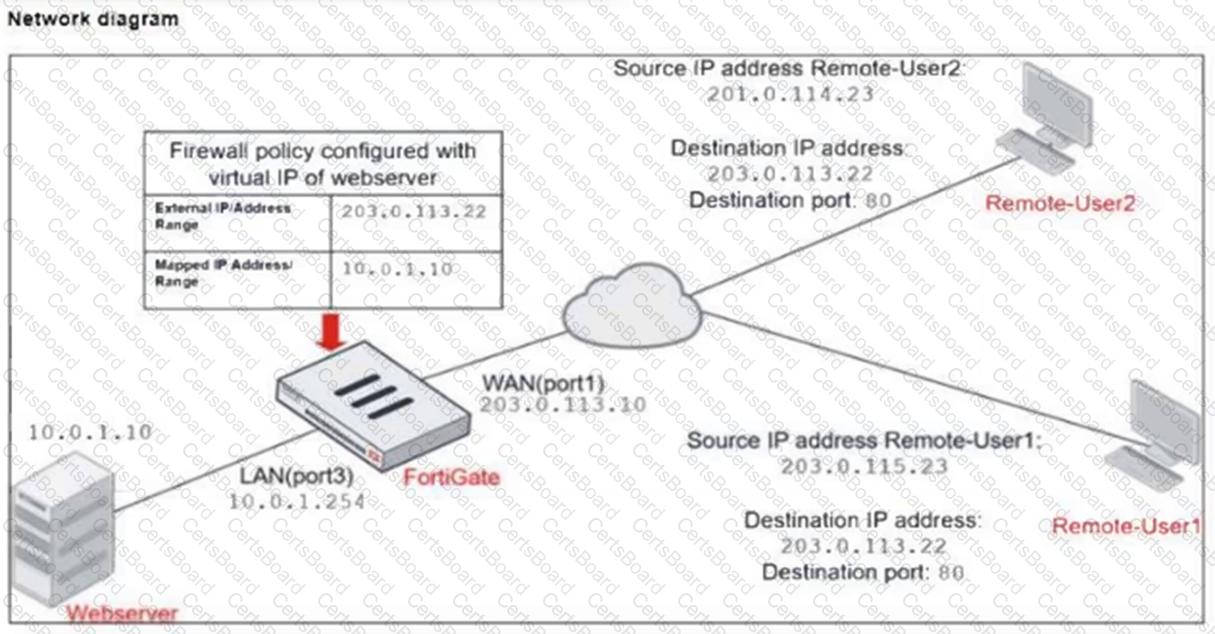
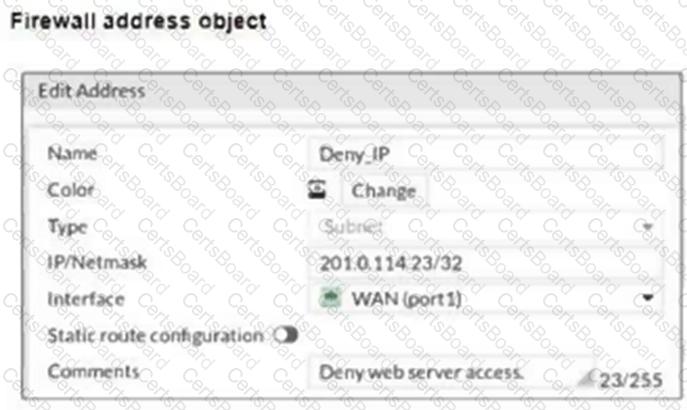
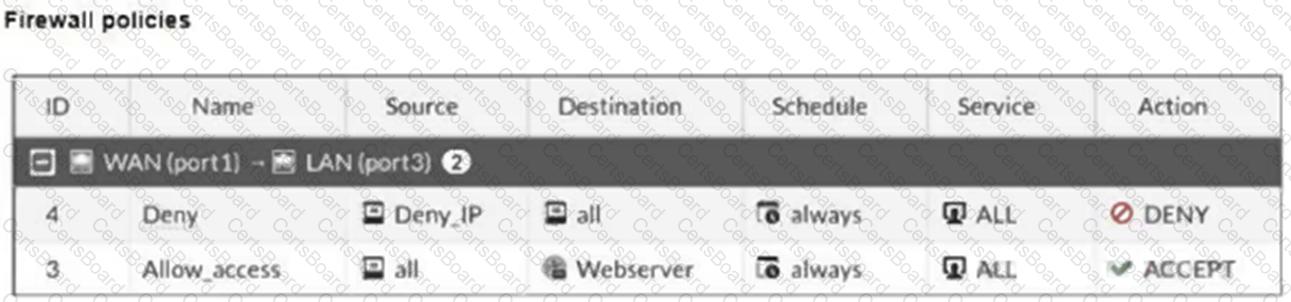
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2? (Choose two.)
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?


