A technician reading workstation security logs notices that an unidentified device is plugged into a USB port several hours a day but is never plugged in when the technician goes to check the machine. File audits reveal nothing unexpected. Which of the following devices is most likely causing this message?
Consider the following statements:
Given the input (userin) of “analyst”, to which of the following would the clearance variable be set?
Given the following pseudocode:
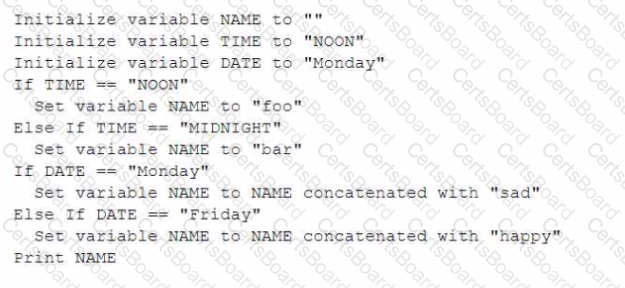
Which of the following would be the output of the program?
An IT manager wants to prevent end users from booting alternative operating systems on workstations. Which of the following security-related best practices would be used to accomplish this?
A computer user is downloading software from the Internet and notices the following at the end of the install file: “…x86.exe”. Which of the following statements BEST represents what the “…x86.exe” means in the installation file?
Which of the following BEST explains the use of float over integer to store monetary values?
A technician is concerned that sensitive data transmitted over the Internet can be intercepted and viewed during
a MITM attack. Which of the following should the technician enable to reduce the risk?
A large payment website was breached recently. A user is concerned that the breach will affect account
security on other sites. Which of the following password best practices would mitigate this risk?


