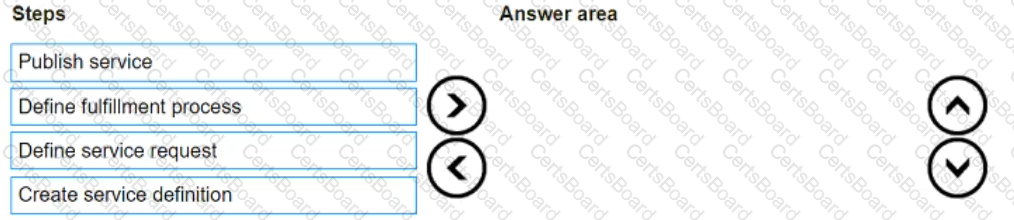
What is the correct sequence of steps in the service catalog design and implementation process?
What is the objective of Confidentiality in information security?
What term refers to the entry points from which an attack can be launched?
What is the effect of a denial-of-service attack?


