An organization wants to manage specialized endpoints and needs a solution that provides the ability to
* Centrally manage configurations
* Push policies.
• Remotely wipe devices
• Maintain asset inventory
Which of the following should the organization do to best meet these requirements?
A company wants to implement hardware security key authentication for accessing sensitive information systems The goal is to prevent unauthorized users from gaining access with a stolen password Which of the following models should the company implement to b«st solve this issue?
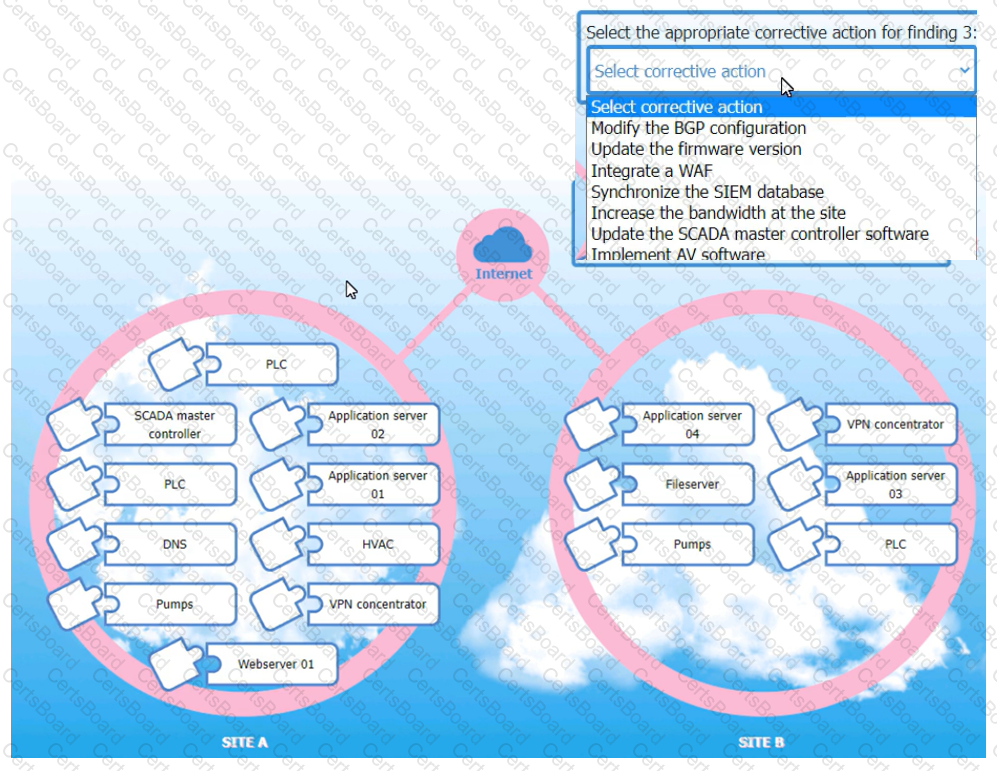
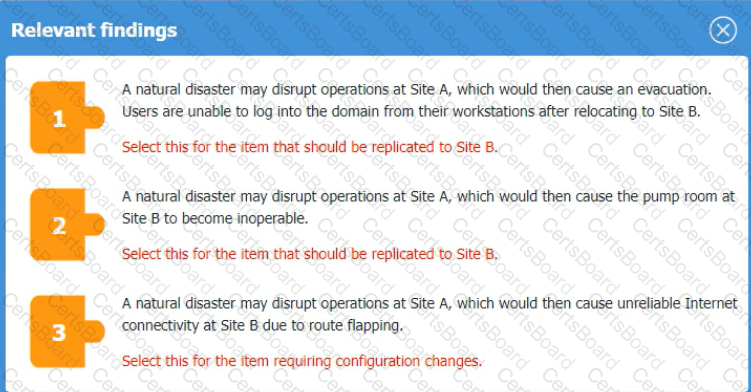
An organization is planning for disaster recovery and continuity of operations, and has noted the following relevant findings:
1. A natural disaster may disrupt operations at Site A, which would then cause an evacuation. Users are
unable to log into the domain from-their workstations after relocating to Site B.
2. A natural disaster may disrupt operations at Site A, which would then cause the pump room at Site B
to become inoperable.
3. A natural disaster may disrupt operations at Site A, which would then cause unreliable internet
connectivity at Site B due to route flapping.
INSTRUCTIONS
Match each relevant finding to the affected host by clicking on the host name and selecting the appropriate number.
For findings 1 and 2, select the items that should be replicated to Site B. For finding 3, select the item requiring configuration changes, then select the appropriate corrective action from the drop-down menu.
A cloud engineer needs to identify appropriate solutions to:
• Provide secure access to internal and external cloud resources.
• Eliminate split-tunnel traffic flows.
• Enable identity and access management capabilities.
Which of the following solutions arc the most appropriate? (Select two).


