A company is deploying new vulnerability scanning software to assess its systems. The current network is highly segmented, and the networking team wants to minimize the number of unique firewall rules. Which of the following scanning techniques would be most efficient to achieve the objective?
A high volume of failed RDP authentication attempts was logged on a critical server within a one-hour period. All of the attempts originated from the same remote IP address and made use of a single valid domain user account. Which of the following would be the most effective mitigating control to reduce the rate of success of this brute-force attack?
Which of the following concepts is using an API to insert bulk access requests from a file into an identity management system an example of?
A technician is analyzing output from a popular network mapping tool for a PCI audit:
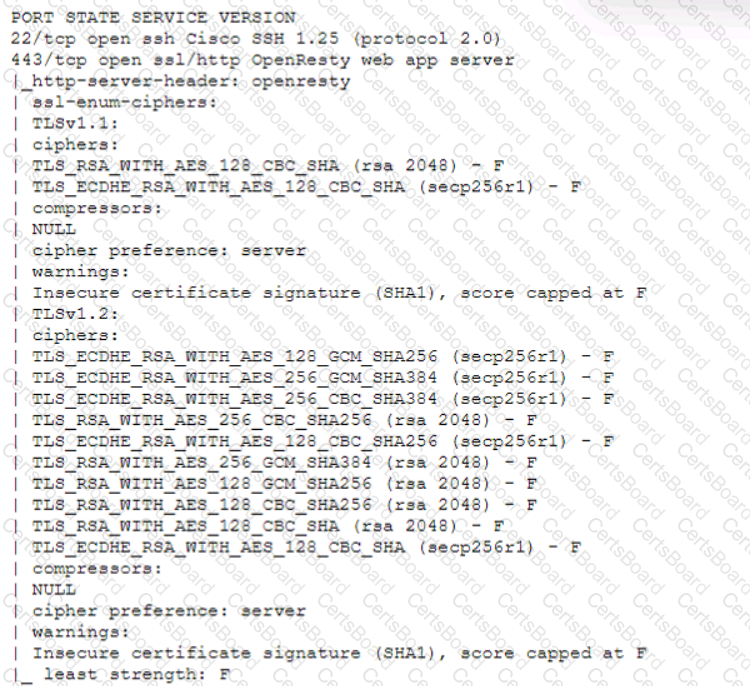
Which of the following best describes the output?


