Refer to the exhibit.
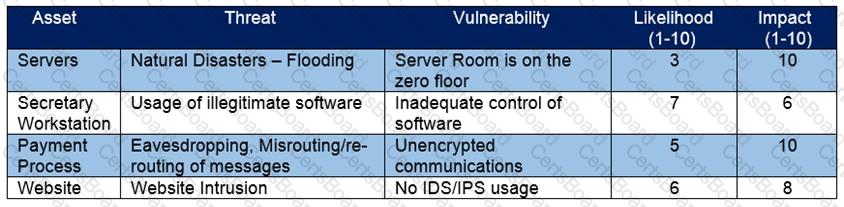
Which asset has the highest risk value?
Refer to the exhibit.
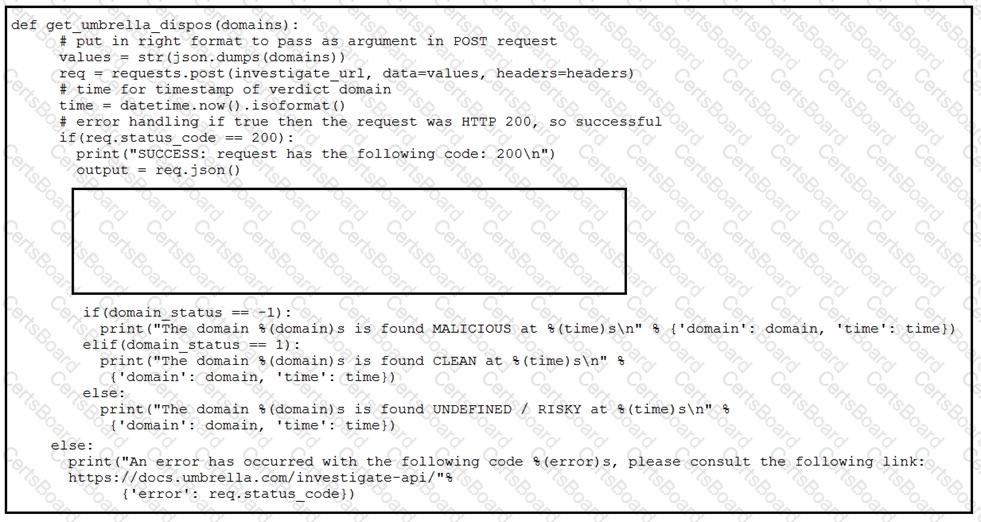
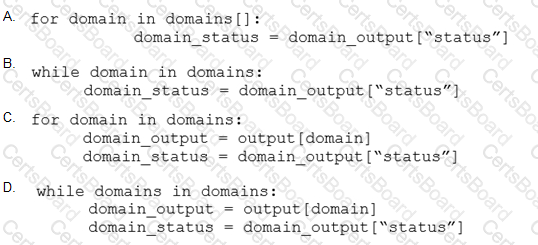
Which code snippet will parse the response to identify the status of the domain as malicious, clean or undefined?
Refer to the exhibit.
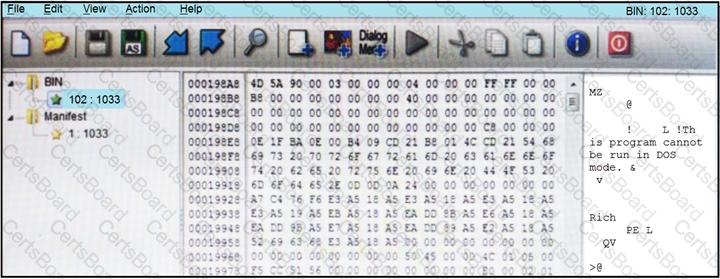
An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
How does Wireshark decrypt TLS network traffic?


