Identify a threat caused, when an attacker sends massive quantities of data to the target with the intention of consuming bandwidth.
Which storage data protection technique provides space-optimal data redundancy to prevent data loss against multiple disk drive failures?
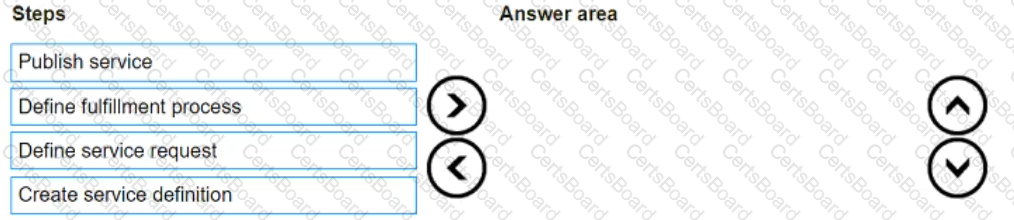
What is the correct sequence of steps in the service catalog design and implementation process?
Which key service management function modifies and aligns services according to consumer needs in the cloud environment?


