A company runs a discussion forum that caters to global users. The company's monitoring system reports that the home page suddenly is seeing elevated response times, even
though internal monitoring has reported no issues or changes. Which of the following is the most likely cause of this issue?
Which of the following Al/ML technologies consumes text input to discern tone?
A systems administrator is configuring backups on a VM and needs the process to run as quickly as possible, reducing the bandwidth on the network during all times from Monday through Saturday. In the event of data corruption, the management team expects the mean time to recovery to be as low as possible. Which of the following backup methods can the administrator use to accomplish these goals?
An e-commerce company is migrating from an on-premises private cloud environment to
a public cloud IaaS environment. You are tasked with right-sizing the environment to
save costs after the migration. The company's requirements are to provide a 20% overhead above the average resource consumption, rounded up.
INSTRUCTIONS
Review the specifications and graphs showing resource usage for the web and database servers. Determine the average resource usage and select the correct specifications from the available drop-down options.
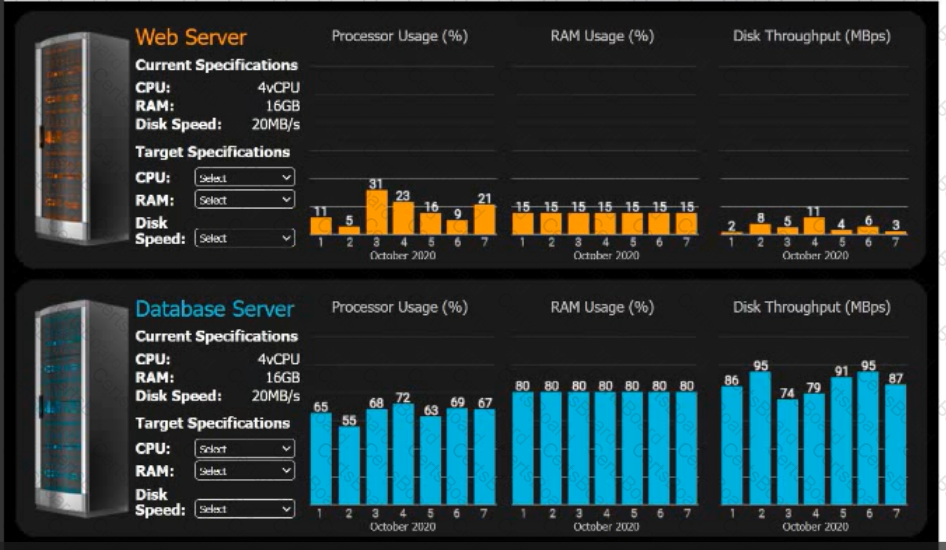
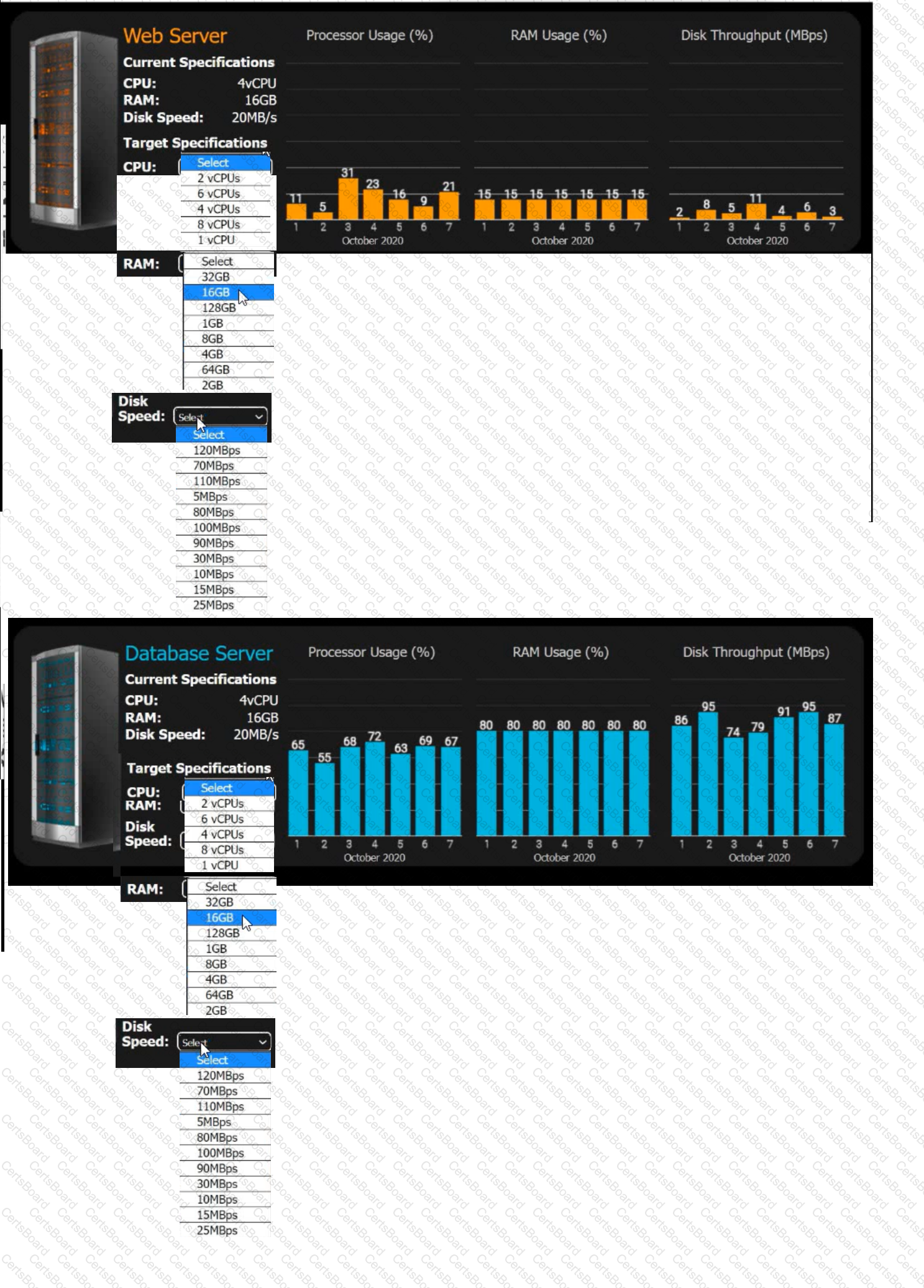
A bank informs an administrator that changes must be made to backups for long-term reporting purposes. Which of the following is the most important change the administrator
should make to satisfy these requirements?
A cloud engineer is collecting web server application logs to troubleshoot intermittent issues. However, the logs are piling up and causing storage issues. Which of the following log
mechanisms should the cloud engineer implement to address this issue?
A cloud security analyst is looking for existing security vulnerabilities on software applications. Which of the following describes this vulnerability management phase?
Which of the following network types allows the addition of new features through the use of network function virtualization?
The change control board received a request to approve a configuration change 10 deploy in the cloud production environment. Which of the following should have already been competed?
An organization's security policy states that software applications should not exchange sensitive data in cleartext. The security analyst is concerned about a software application that uses Base64 to encode credit card data. Which of the following would be the best algorithm to replace Base64?