An analyst needs to provide recommendations based on a recent vulnerability scan:
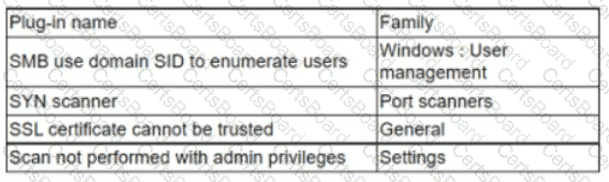
Which of the following should the analyst recommend addressing to ensure potential vulnerabilities are identified?
Which of the following would likely be used to update a dashboard that integrates…..
A security analyst is trying to validate the results of a web application scan with Burp Suite. The security analyst performs the following:
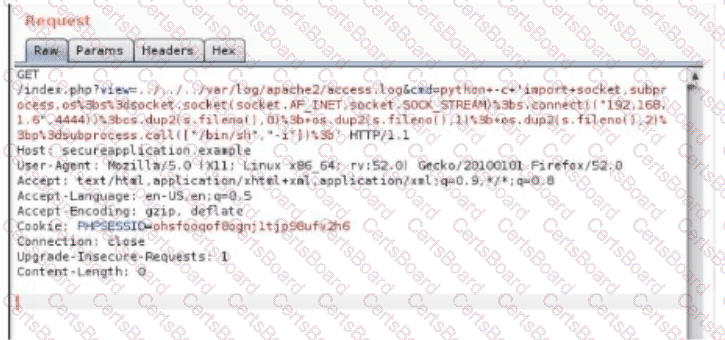
Which of the following vulnerabilitles Is the securlty analyst trylng to valldate?
A security audit for unsecured network services was conducted, and the following output was generated:
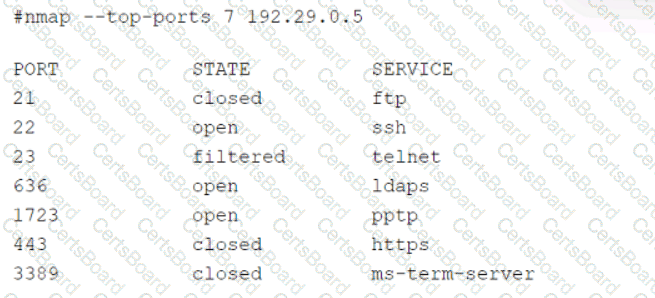
Which of the following services should the security team investigate further? (Select two).
A cybersecurity team lead is developing metrics to present in the weekly executive briefs. Executives are interested in knowing how long it takes to stop the spread of malware that enters the network.
Which of the following metrics should the team lead include in the briefs?
Which of the following threat-modeling procedures is in the OWASP Web Security Testing Guide?
An XSS vulnerability was reported on one of the public websites of a company. The security department confirmed the finding and needs to provide a recommendation to the application owner. Which of the following recommendations will best prevent this vulnerability from being exploited? (Select two).
A penetration tester is conducting a test on an organization's software development website. The penetration tester sends the following request to the web interface:
Which of the following exploits is most likely being attempted?
Which of the following risk management principles is accomplished by purchasing cyber insurance?


