Bob has been hired to do a web application security test. Bob notices that the site is dynamic and must make use of a back end database. Bob wants to see if SQL Injection would be possible. What is the first character that Bob should use to attempt breaking valid SQL request?
Fred is scanning his network to ensure it is as secure as possible. Fred sends a TCP probe packet to a host with a FIN flag and he receives a RST/ACK response. What does this mean?
What is the name of the international standard that establishes a baseline level of confidence in the security functionality of IT products by providing a set of requirements for evaluation?
You have initiated an active operating system fingerprinting attempt with nmap against a target system:
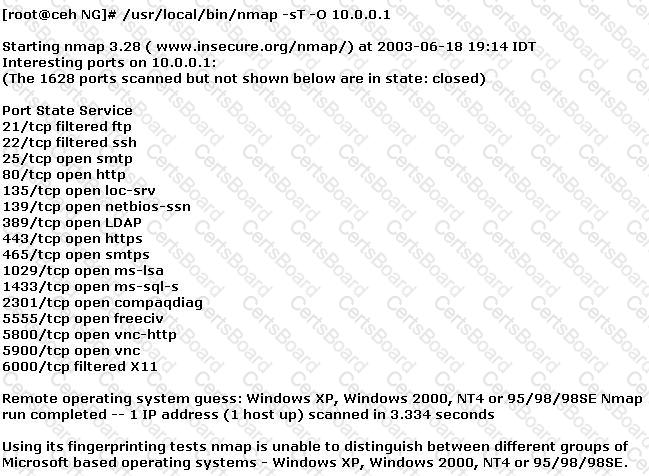
What operating system is the target host running based on the open ports shown above?
A recently hired network security associate at a local bank was given the responsibility to perform daily scans of the internal network to look for unauthorized devices. The employee decides to write a script that will scan the network for unauthorized devices every morning at 5:00 am.
Which of the following programming languages would most likely be used?
Network Administrator Patricia is doing an audit of the network. Below are some of her findings concerning DNS. Which of these would be a cause for alarm?
Select the best answer.
Which of the following are advantages of adopting a Single Sign On (SSO) system? (Choose two.)
Which system consists of a publicly available set of databases that contain domain name registration contact information?


