A web application is susceptible to cross-site scripting. Which two methods allow this issue to be mitigated? (Choose two.)
Refer to the exhibit.

Which code snippet must be added to the blank in the code to automate the evaluation and handling of errors due to wrong credentials when Basic Authorization is used?
A)

B)

C)

D)

Which tool is used to deploy an IOx application to a group of lOx devices at one time?
An enterprise refactors its monolithic application into a modem cloud-native application that is based on microservices. A key requirement of the application design is to ensure that the IT team is aware of performance issues or bottlenecks in the new application Which two approaches must be part of the design considerations'' (Choose two.)
Which OAuth mechanism enables clients to continue to have an active access token without further interaction from the user?
Drag and drop the code from the bottom onto the box where the code is missing in the Python code to query for user permissions while mitigating against SQL Injection Not all options are used.

Drag and drop the code onto the snippet to update a SSID in Meraki using the Dashboard API. Not all options are used.

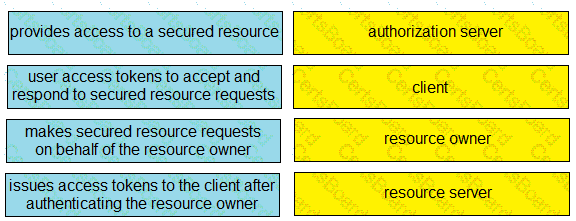
Drag and drop the descriptions from the left onto the related OAuth-defined roles on the right.
A developer must deploy a containerized application for network device inventory management. The developer sets up a Kubernetes cluster on two separate hypervisors The SLA is not currently meeting a specified maximum value for network latency/jitter. CPU/memory and disk 1,0 are functioning property.
Which two design approaches resolve the issue? (Choose two.)


