An engineer has created a bash script to automate a complicated process. During script execution, this error occurs: permission denied. Which command must be added to execute this script?
Refer to the exhibit.
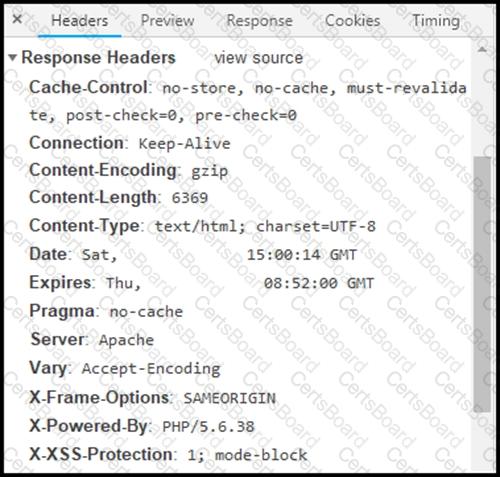
Where are the browser page rendering permissions displayed?