Which of the following DFD component is used to represent the change in privilege levels?
Which of the following state management method works only for a sequence of dynamically generated forms?
Jacob, a Security Engineer of the testing team, was inspecting the source code to find security vulnerabilities.
Which type of security assessment activity Jacob is currently performing?
Alice, a security engineer, was performing security testing on the application. He found that users can view the website structure and file names. As per the standard security practices, this can pose a serious security risk as attackers can access hidden script files in your directory. Which of the following will mitigate the above security risk?
Which of the following configurations can help you avoid displaying server names in server response header?
Which of the following relationship is used to describe security use case scenario?
In a certain website, a secure login feature is designed to prevent brute-force attack by implementing account lockout mechanism. The account will automatically be locked after five failed attempts. This feature will not allow the users to login to the website until their account is unlocked. However, there is a possibility that this security feature can be abused to perform __________ attack.
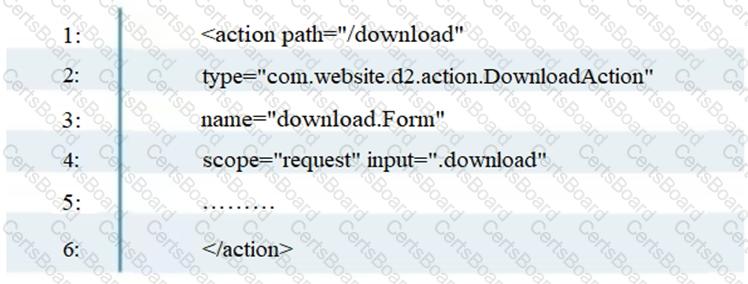
To enable the struts validator on an application, which configuration setting should be applied in the struts validator configuration file?
The threat modeling phase where applications are decomposed and their entry points are reviewed from an attacker's perspective is known as ________


