A computer forensics investigator is inspecting the firewall logs for a large financial institution that has employees working 24 hours a day, 7 days a week.
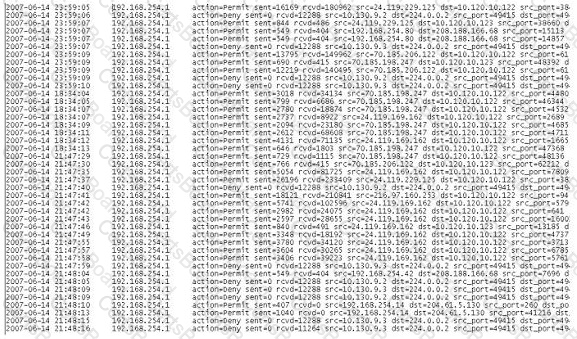
What can the investigator infer from the screenshot seen below?
Which among the following files provides email header information in the Microsoft Exchange server?
While looking through the IIS log file of a web server, you find the following entries:

What is evident from this log file?
Which of the following are small pieces of data sent from a website and stored on the user’s computer by the user’s web browser to track, validate, and maintain specific user information?
When reviewing web logs, you see an entry for resource not found in the HTTP status code filed.
What is the actual error code that you would see in the log for resource not found?
Richard is extracting volatile data from a system and uses the command doskey/history. What is he trying to extract?
Which password cracking technique uses every possible combination of character sets?
Before performing a logical or physical search of a drive in Encase, what must be added to the program?


