Which of the following is a correct flow of the stages in an incident handling and response (IH&R) process?
Which of the following service provides phishing protection and content filtering to manage the Internet experience on and off your network with the acceptable use or compliance policies?
Which of the following security technology is used to attract and trap people who attempt unauthorized or illicit utilization of the host system?
A type of threat intelligent that find out the information about the attacker by misleading them is known as
.
An organization is implementing and deploying the SIEM with following capabilities.
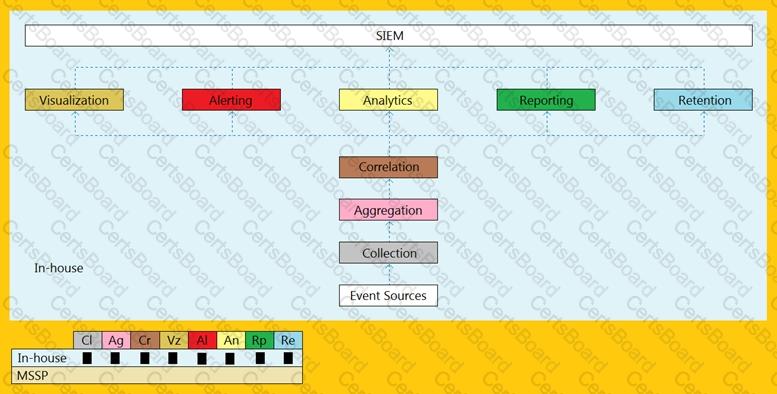
What kind of SIEM deployment architecture the organization is planning to implement?
An attacker, in an attempt to exploit the vulnerability in the dynamically generated welcome page, inserted code at the end of the company’s URL as follows:
http://technosoft.com.com/ . Identify the attack demonstrated in the above scenario.