URL Filtering employs a technology, which educates users on web usage policy in real time. What is the name of that technology?
Which is a main component of the Check Point security management architecture?
What licensing feature is used to verify licenses and activate new licenses added to the License and Contracts repository?
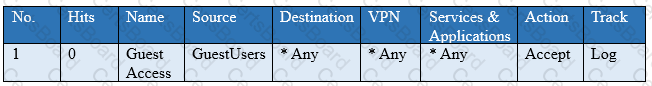
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?
Fill in the blanks: A ____ license requires an administrator to designate a gateway for attachment whereas a _____ license is automatically attached to a Security Gateway.
Fill in the blank: In Security Gateways R75 and above, SIC uses ______________ for encryption.
Which option, when applied to a rule, allows all encrypted and non-VPN traffic that matches the rule?
Which Check Point supported authentication scheme typically requires a user to possess a token?


