Refer to the exhibits.
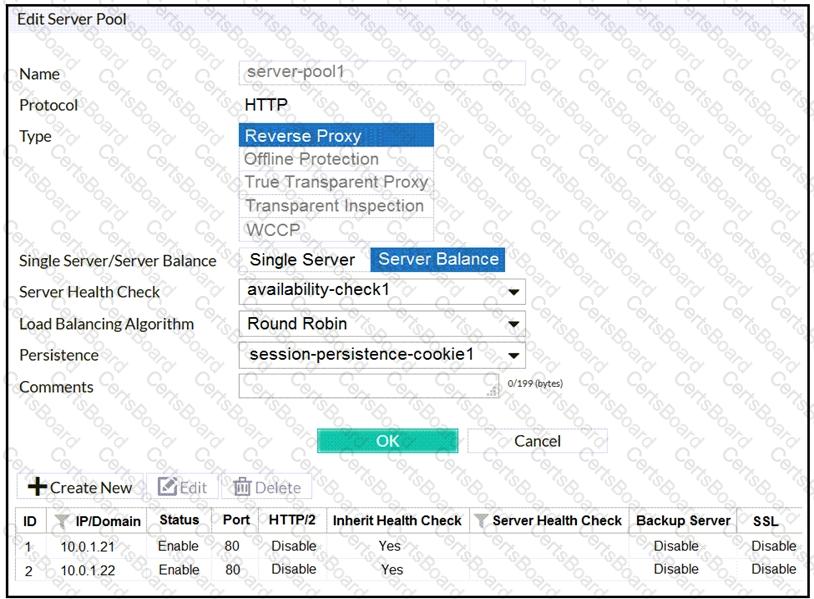
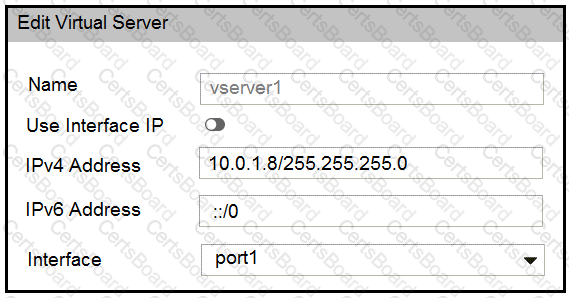
FortiWeb is configured in reverse proxy mode and it is deployed downstream to FortiGate. Based on the configuration shown in the exhibits, which of the following statements is true?
Which two statements about the anti-defacement feature on FortiWeb are true? (Choose two.)
True transparent proxy mode is best suited for use in which type of environment?
You’ve configured an authentication rule with delegation enabled on FortiWeb.
What happens when a user tries to access the web application?


