Examine the FortiMail recipient-based policy shown in the exhibit; then answer the question below.
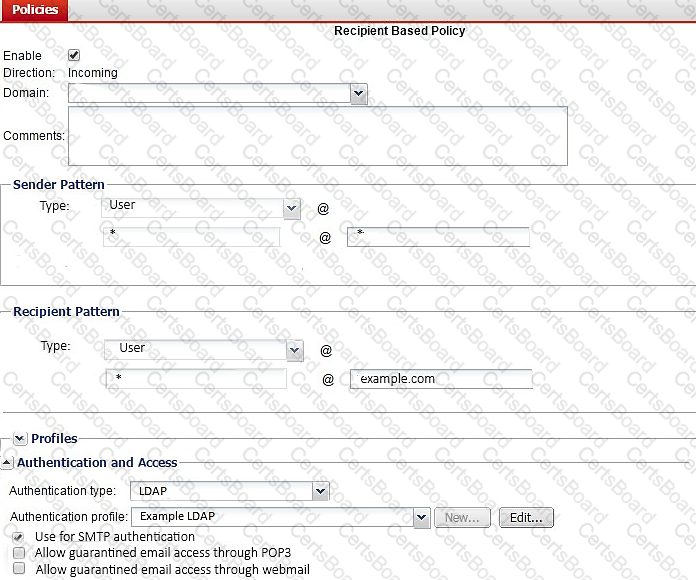
After creating the policy, an administrator discovered that clients are able to send unauthenticated email using SMTP. What must be done to ensure clients cannot send unauthenticated email?
Examine the FortiMail active-passive cluster shown in the exhibit; then answer the question below.
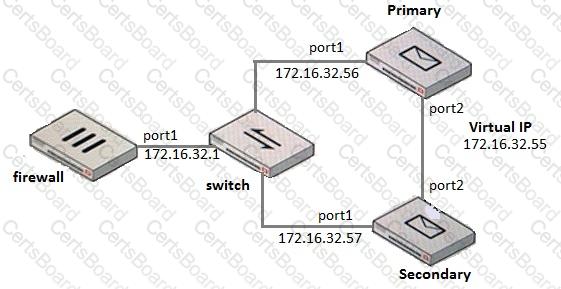
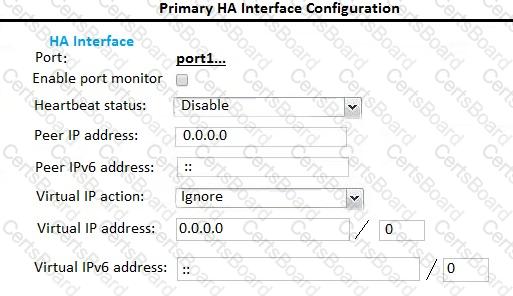
Which of the following parameters are recommended for the Primary FortiMail’s HA interface configuration? (Choose three.)
Examine the FortiMail DLP scan rule shown in the exhibit; then answer the question below.
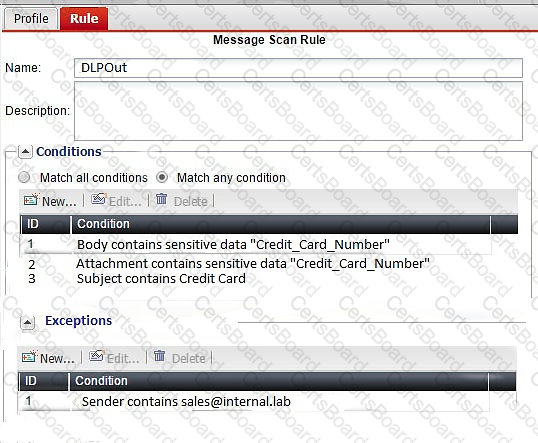
Which of the following statements is true regarding this configuration? (Choose two.)
Examine the message column of a log cross search result of an inbound email shown in the exhibit; then answer the question below
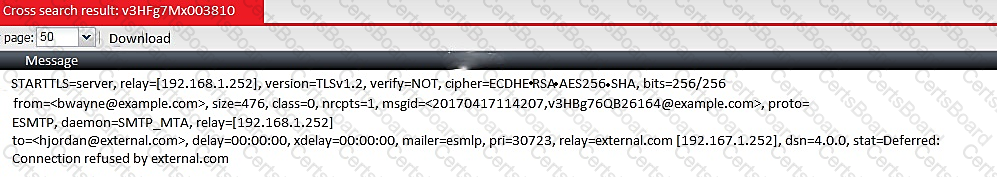
Based on logs, which of the following statements are true? (Choose two.)
FortiMail is configured with the protected domain example.com.
Which two envelope addresses will require an access receive rule, to relay for unauthenticated senders? (Choose two.)
Which FortiMail option removes embedded code components in Microsoft Word, while maintaining the original file format?
Which two features are available when you enable HA centralized monitoring on FortiMail? (Choose two.)
Refer to the exhibit.

What are two expected outcomes if FortiMail applies this antivirus action profile to an email? (Choose two.)


