An administrator notices multiple IP addresses attempting to log in to an application frequently, within a short time period. They suspect attackers are attempting to guess user passwords for a secure application.
What is the best way to limit this type of attack on FortiWeb, while still allowing legitimate traffic through?
Refer to the exhibit.
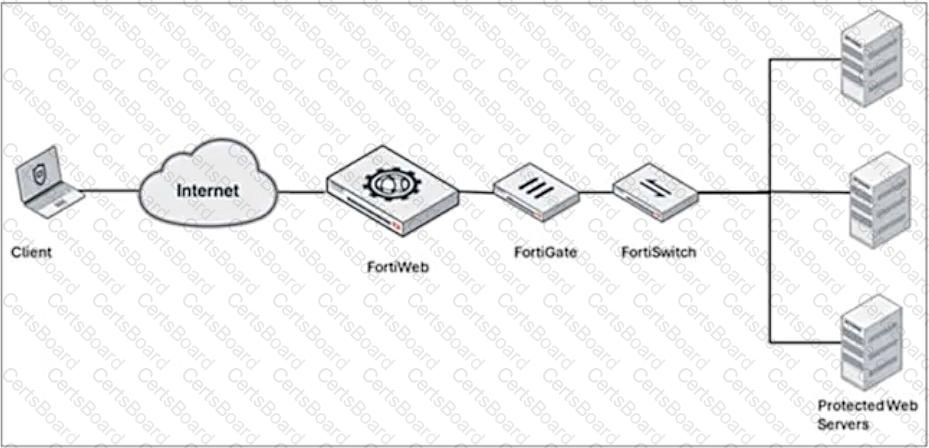
A FortiWeb device is deployed upstream of a device performing source network address translation (SNAT) or load balancing.
What configuration must you perform on FortiWeb to preserve the original IP address of the client?
Under which two circumstances does FortiWeb use its own certificates? (Choose two.)
Which implementation is most suited for a deployment that must meet PCI DSS compliance criteria?
Which high availability mode is commonly used to integrate with a traffic distributer like FortiADC?
Refer to the exhibit.
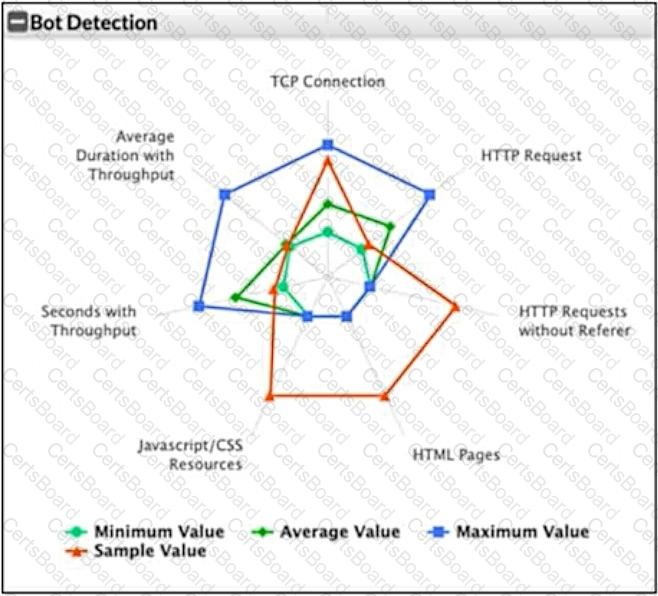
What can you conclude from this support vector machine (SVM) plot of a potential bot connection?
How are bot machine learning (ML) models different from API or anomaly detection models?


