The monitor traffic interface command is being used to capture the packets destined to and the from the SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
Exhibit
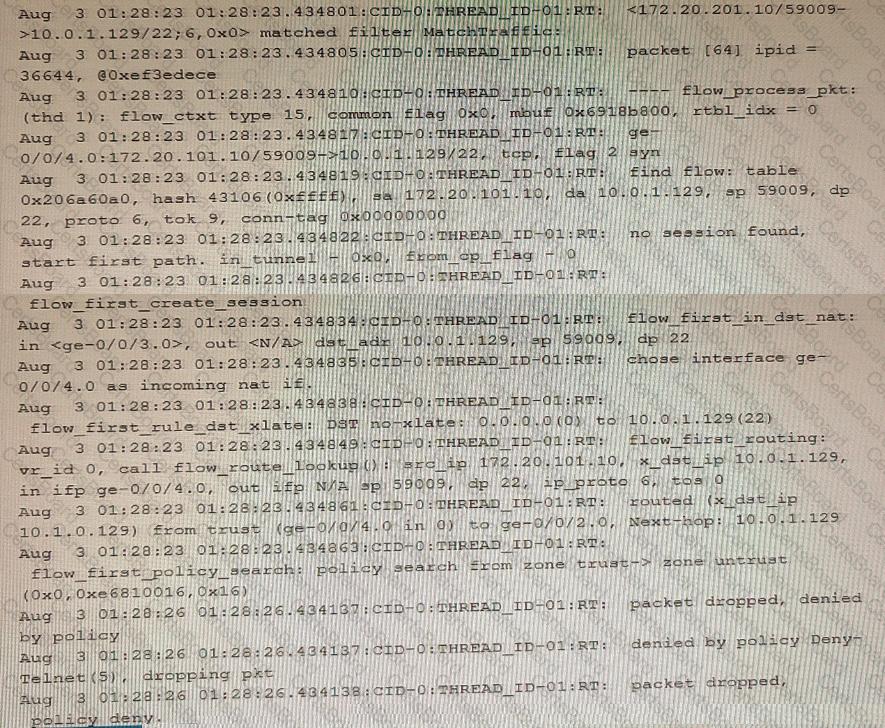
Which two statements are correct about the output shown in the exhibit. (Choose two.)
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data traffic. How many IKE security associations are required between the IPsec peers in this scenario?


