In a campus network design, what are two benefits of using BFD for failure detection'? (Choose two.)
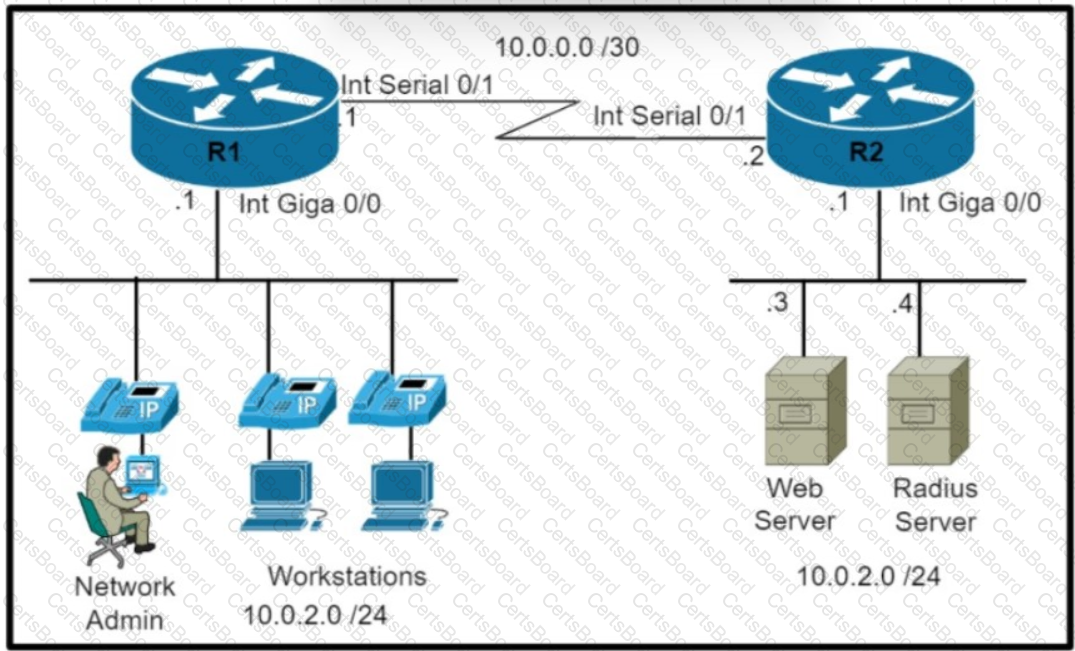
Refer to the exhibit Which command set is required on router R1 to allow the network administrator to authenticate via RADIUS'?

Which component of the Cisco Cyber Threat Defense solution provides user and flow context analysis?
Refer to the exhibit.

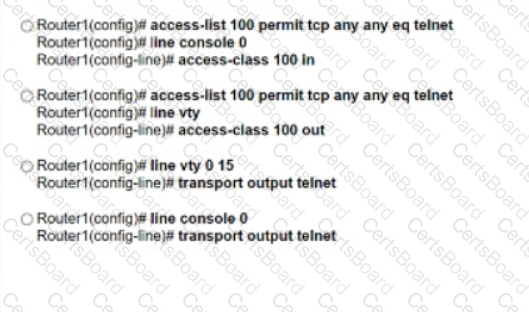
An engineer attempts to connect to another device from Route1’s console port. Which configuration is needed to allow telnet connections?