Which document provides information on best practices for writing Splunk-based hunting queries, predefined queries which may be customized to hunt for suspicious network connections, and predefined queries which may be customized to hunt for suspicious processes?
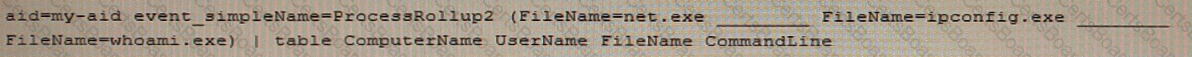
Adversaries commonly execute discovery commands such as netexe, ipconfig.exe, and whoami exe. Rather than query for each of these commands individually, you would like to use a single query with all of them. What Splunk operator is needed to complete the following query?
What do you click to jump to a Process Timeline from many pages in Falcon, such as a Hash Search?
What information is provided from the MITRE ATT&CK framework in a detection's Execution Details?
You want to produce a list of all event occurrences along with selected fields such as the full path, time, username etc.Which command would be the appropriate choice?
Which threat framework allows a threat hunter to explore and model specific adversary tactics and techniques, with links to intelligence and case studies?
The Events Data Dictionary found in the Falcon documentation is useful for writing hunting queries because:


