Which tool is best suited for identifying applications and code on a Web server that can lead to a SQL injection attack?
Consider the following image of a packet capture:
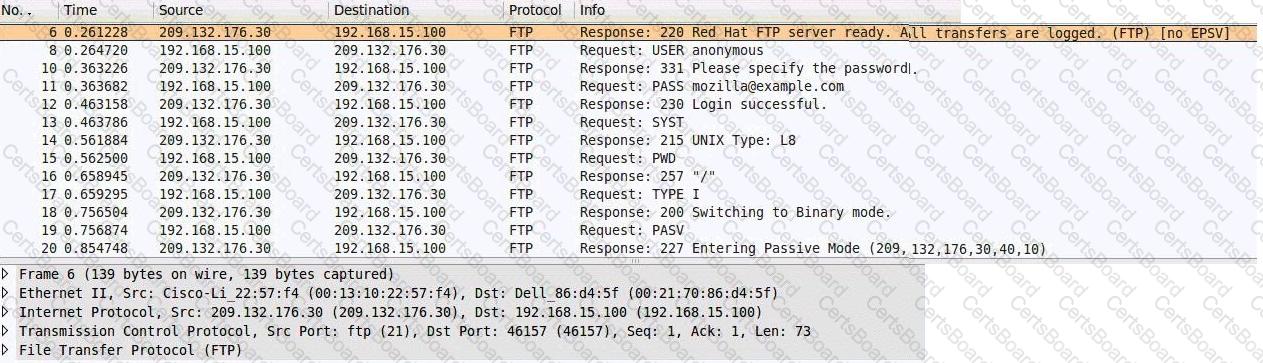
Which of the following best describes the protocol used, along with its primary benefit?
A new video conferencing device has been installed on the network. You have been assigned to troubleshoot a connectivity problem between remote workers and the central company. Specifically, remote workers are having problems making any connection at all. Which technique will most likely help you solve this problem while retaining the existing level of security at the firewall?
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?
You have been assigned to provide security measures for your office's reception area. Although the company needs to provide security measures, costs must be kept to a minimum. Which of the following tools is the most appropriate choice?
You are using a PKI solution that is based on Secure Sockets Layer (SSL). Which of the following describes the function of the asymmetric-key-encryption algorithm used?
Which of the following is the most likely first step to enable a server to recover from a denial-of-service attack in which all hard disk data is lost?
A disgruntled employee has discovered that the company Web server is not protected against a particular buffer overflow vulnerability. The disgruntled employee has created an application to take advantage of this vulnerability and secretly obtain sensitive data from the Web server's hard disk. This application sends a set of packets to the Web server that causes it to present an unauthenticated terminal with root privileges. What is the name for this particular type of attack?